In today’s digital age, cyber security is more critical than ever. With increasing cyber threats and sophisticated attacks, protecting sensitive information and ensuring online safety are paramount. Organizations, from small businesses to large enterprises, rely on robust cyber security measures to safeguard their data and maintain trust with their users. Cyber security professionals are on the front lines, defending against cyber threats and securing digital infrastructures.
Google stands out as a leader in the cyber security field for several reasons. As one of the largest tech companies globally, Google invests heavily in cutting-edge technologies and innovative solutions to tackle cyber threats.
Their commitment to security is evident in their comprehensive approach, including advanced threat detection systems, continuous monitoring, and a team of highly skilled security experts. Google’s dedication to staying ahead of emerging threats and its emphasis on creating a secure environment for its users make it a top choice for those seeking careers in cyber security.
What is Cyber Security?
Definition and Significance
Cyber security refers to the practice of protecting systems, networks, and data from digital attacks, theft, and damage. It encompasses a range of technologies, processes, and practices designed to ensure the confidentiality, integrity, and availability of information. As our reliance on digital systems grows, cyber security has become crucial in defending against various threats, including hacking, malware, phishing, and other cyber crimes. Effective cyber security helps safeguard personal and organizational data, maintain privacy, and ensure that digital operations run smoothly without disruptions.
Basic Concepts Every Job Seeker Should Know
- Confidentiality, Integrity, and Availability (CIA Triad): The CIA triad is the foundational principle of cyber security. Confidentiality ensures that information is accessible only to those authorized to see it. Integrity involves maintaining the accuracy and completeness of data. Availability ensures that information and resources are accessible to authorized users when needed.
- Threats and Vulnerabilities: Understanding common cyber threats (e.g., viruses, ransomware, phishing) and vulnerabilities (e.g., weak passwords, unpatched software) is essential. Threats are potential dangers that could exploit vulnerabilities to cause harm.
- Firewalls and Encryption: Firewalls are security systems that monitor and control incoming and outgoing network traffic based on predetermined security rules. Encryption involves converting data into a coded format to prevent unauthorized access.
- Authentication and Authorization: Authentication verifies the identity of users or systems, while authorization determines what actions an authenticated user is permitted to perform. These processes help ensure that only authorized individuals can access sensitive information.
- Incident Response and Management: This involves preparing for and responding to cyber security incidents. It includes identifying, managing, and mitigating security breaches or attacks to minimize damage and recover quickly.
Why Work in Cyber Security at Google?

Google’s Reputation in the Industry
Google is renowned for its innovation and leadership in technology, and its cyber security division is no exception. The company is a global leader in internet services and cloud computing, and it has built a strong reputation for its commitment to security and privacy. Google’s cyber security team is at the forefront of developing and implementing cutting-edge technologies to protect against evolving threats.
Their proactive approach to security, coupled with their substantial investment in research and development, positions Google as a key player in the industry. Working at Google means being part of a team that sets the standard for excellence in cyber security and contributes to global internet safety. For those interested in starting a new venture, understanding Travel Agency Startup Costs can provide valuable insights into business planning and financial management.
Benefits and Perks of Working at Google
Google offers a range of benefits and perks that make it an attractive place to work. Employees enjoy competitive salaries and comprehensive health benefits, including medical, dental, and vision coverage. Google’s commitment to work-life balance is reflected in their flexible work arrangements and generous paid time off. The company also provides opportunities for professional growth through ongoing training and development programs. Additionally, Google’s unique work environment includes perks such as on-site wellness centers, free meals, and various employee resources aimed at promoting overall well-being. These benefits, combined with a culture of innovation and collaboration, make Google a top choice for those pursuing a career in cyber security.
Types of Cyber Security Jobs at Google
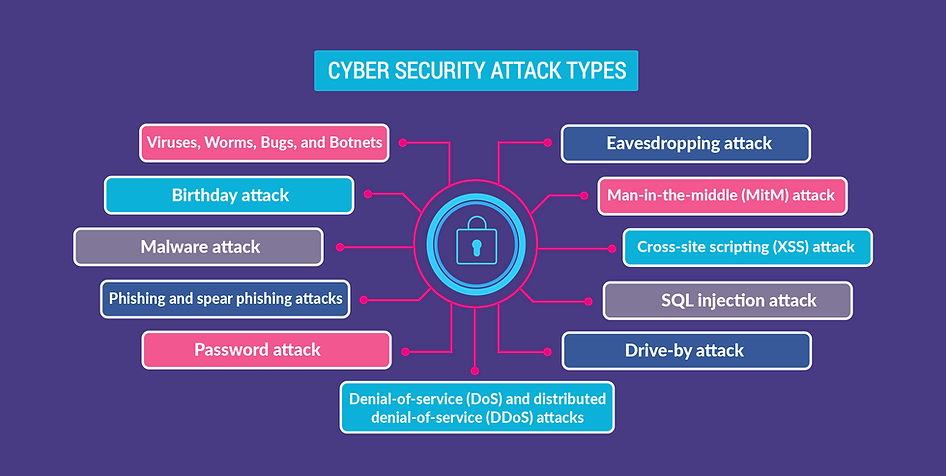
Overview of Different Roles
- Security Engineer: Security Engineers are responsible for designing and implementing security measures to protect Google’s systems and data. They work on developing secure software, identifying vulnerabilities, and responding to security incidents. This role requires a strong understanding of network security, encryption, and threat modeling.
- Threat Analyst: Threat Analysts focus on monitoring and analyzing potential security threats. They use various tools and techniques to detect and investigate suspicious activities, assess risks, and recommend countermeasures. A deep knowledge of cyber threat intelligence and incident response is essential for this role.
- Security Operations Center (SOC) Analyst: SOC Analysts work in a high-paced environment to monitor and respond to security incidents in real-time. They analyze security alerts, conduct investigations, and coordinate with other teams to mitigate threats. This role demands strong analytical skills and experience with security information and event management (SIEM) systems.
- Incident Responder: Incident Responders handle the aftermath of security breaches or attacks. They lead efforts to contain, analyze, and recover from incidents, working closely with other teams to prevent future occurrences. This role requires expertise in forensic analysis, incident management, and crisis communication.
Skills and Qualifications Needed for Each Role
- Security Engineer: Required skills include proficiency in programming languages (e.g., Python, Java), experience with security tools and technologies, and a strong understanding of network protocols and security best practices. Relevant certifications, such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH), can be advantageous.
- Threat Analyst: Key qualifications include expertise in threat intelligence platforms, knowledge of cyber attack vectors, and experience with data analysis. Certifications like Certified Threat Intelligence Analyst (CTIA) or GIAC Cyber Threat Intelligence (GCTI) can enhance credibility.
- SOC Analyst: Essential skills include familiarity with SIEM tools, experience with incident detection and response, and strong problem-solving abilities. Certifications such as CompTIA Security+ or Certified Information Security Manager (CISM) are beneficial.
- Incident Responder: Important qualifications include skills in forensic investigation, incident management, and understanding of malware analysis. Certifications like Certified Incident Handler (GCIH) or Certified Forensic Computer Examiner (CFCE) can be valuable.
How to Find Google Cyber Security Jobs
Tips for Searching Job Listings
- Use Specific Keywords: When searching for cyber security jobs, use specific keywords like “Google Cyber Security Engineer” or “Google Threat Analyst” to find relevant listings. Incorporate terms related to different cyber security roles and technologies to narrow down your search.
- Leverage Job Boards and Professional Networks: Platforms like LinkedIn, Indeed, and Glassdoor often list job openings at Google. Set up job alerts to receive notifications about new postings in the cyber security field. Additionally, join professional networks and forums to stay updated on job opportunities and industry trends.
- Check Google’s Career Page Regularly: Google’s career page is a primary source for job listings. Regularly visit the page to view the latest openings and learn about different roles within the company. Explore the “Life at Google” section to understand the company culture and work environment.
- Attend Industry Events and Meetups: Participating in cyber security conferences, webinars, and meetups can provide networking opportunities and insights into job openings. Google often sponsors or attends these events, offering a chance to connect with recruiters and learn about potential opportunities.
- Network with Current Employees: Reach out to Google employees or alumni in the cyber security field. Informational interviews and networking can provide valuable insights into the application process and company culture, as well as potential job leads.
How to Navigate Google’s Career Portal
- Visit the Google Careers Website: Go to Google’s career portal to start your job search. Use the search bar to enter relevant job titles or keywords related to cyber security.
- Filter Job Listings: Use the available filters to narrow down your search based on location, job type, and experience level. This helps in finding roles that match your qualifications and preferences.
- Read Job Descriptions Carefully: Review job descriptions to understand the responsibilities, qualifications, and skills required for each role. Tailor your resume and application to align with the specific requirements mentioned.
- Create a Google Careers Profile: Set up a profile to apply for jobs and manage your applications. This allows you to save job listings, track application status, and receive job alerts based on your preferences.
- Follow Application Instructions: Ensure you follow the application instructions precisely. Submit your resume, cover letter, and any additional documents as required. Pay attention to any specific questions or prompts in the application.
Application Process for Google Cyber Security Jobs
Step-by-Step Guide on Applying
- Prepare Your Resume and Cover Letter: Tailor your resume and cover letter to highlight your relevant experience, skills, and achievements in cyber security. Emphasize any certifications or projects that align with the role you are applying for.
- Submit Your Application: Apply through Google’s career portal by selecting the job listing and following the instructions to submit your application. Ensure all required fields are completed and documents are uploaded.
- Receive Confirmation: After submitting your application, you should receive a confirmation email. This email will acknowledge receipt of your application and provide information on the next steps.
- Prepare for Initial Screening: If selected, you will undergo an initial screening, which may include a phone or video interview with a recruiter. Be prepared to discuss your background, skills, and interest in the role.
- Interview Process: The interview process typically involves multiple stages, including technical interviews, behavioral interviews, and assessments. You may be asked to solve technical problems, discuss your experience in cyber security, and demonstrate your problem-solving abilities.
- Follow Up: After your interviews, follow up with a thank-you email to express your appreciation for the opportunity. This reinforces your interest in the position and helps keep you top of mind.
Common Requirements and What to Expect During the Interview

- Technical Skills: Expect to be tested on your technical skills relevant to the role, such as knowledge of security protocols, threat analysis, and incident response. Be ready to solve problems and discuss your approach to cyber security challenges.
- Behavioral Questions: Prepare for behavioral questions that assess your ability to handle real-world scenarios, work under pressure, and collaborate with teams. Reflect on past experiences where you demonstrated key skills.
- Cultural Fit: Google values cultural fit and collaboration. Expect questions that gauge your alignment with Google’s values and work environment. Demonstrate your adaptability, creativity, and enthusiasm for the role.
- Certifications and Education: Ensure you have relevant certifications (e.g., CISSP, CEH) and educational qualifications. These are often prerequisites and can be discussed during the interview to validate your expertise.
Key Skills and Qualifications for Cyber Security Jobs
Essential Skills
- Threat Analysis: The ability to identify and assess potential security threats is crucial. This includes understanding various types of cyber threats, such as malware, phishing, and ransomware, and analyzing their potential impact on systems and data.
- Network Security: Proficiency in protecting and managing network infrastructure is essential. This involves configuring and monitoring firewalls, intrusion detection systems, and virtual private networks (VPNs) to prevent unauthorized access and ensure network integrity.
- Incident Response: Effective incident response skills involve identifying, managing, and mitigating security breaches or attacks. This includes conducting forensic investigations, coordinating with other teams, and implementing recovery strategies to minimize damage.
- Penetration Testing: Knowledge of penetration testing techniques is valuable for identifying vulnerabilities in systems before malicious actors can exploit them. This includes conducting ethical hacking exercises and using tools to simulate attacks.
- Security Policy and Compliance: Understanding and implementing security policies and ensuring compliance with industry standards and regulations (e.g., GDPR, HIPAA) is important for maintaining a secure and legally compliant environment.
- Cryptography: Familiarity with encryption methods and protocols is essential for protecting data confidentiality and integrity. This includes implementing and managing cryptographic techniques to secure communications and stored data.
Educational Background and Certifications
- Degree in Cyber Security or Related Field: A bachelor’s or master’s degree in cyber security, computer science, information technology, or a related field provides a strong foundation in technical knowledge and problem-solving skills.
- Certifications:
- Certified Information Systems Security Professional (CISSP): Recognized globally, this certification validates your ability to manage and implement security policies and procedures.
- Certified Ethical Hacker (CEH): This certification demonstrates your skills in ethical hacking and penetration testing techniques.
- Certified Information Security Manager (CISM): Focuses on information risk management and governance, making it valuable for managerial roles.
- CompTIA Security+: A fundamental certification that covers basic security concepts and practices, ideal for entry-level positions.
- Continuous Learning: Cyber security is a rapidly evolving field, so continuous learning and staying updated with the latest trends and technologies is crucial. Advanced certifications and specialized training can further enhance your qualifications.
Preparing for a Cyber Security Role at Google
Recommended Resources and Tools
- Online Courses and Training: Platforms like Coursera, Udemy, and LinkedIn Learning offer courses on various cyber security topics. Enroll in courses that cover areas such as network security, threat analysis, and incident response to build your skills.
- Books and Publications: Read books and industry publications to deepen your knowledge. Some recommended reads include “The Art of Invisibility” by Frank Ahearn and “Cybersecurity and Cyberwar” by P.W. Singer and Allan Friedman.
- Security Tools and Software: Familiarize yourself with popular security tools and software, such as Wireshark (network analysis), Metasploit (penetration testing), and Splunk (log management). Hands-on experience with these tools will be beneficial.
- Practice Labs and Simulations: Use virtual labs and simulation environments to practice your skills. Platforms like TryHackMe and Hack The Box offer interactive challenges and scenarios to test your abilities.
How to Stay Updated with the Latest Trends in Cyber Security
- Follow Industry News: Stay informed about the latest developments and trends in cyber security by following reputable news sources and blogs, such as Krebs on Security and The Hacker News.
- Join Professional Organizations: Participate in professional organizations like (ISC)², ISACA, and the Information Systems Security Association (ISSA). These organizations provide valuable resources, networking opportunities, and access to industry events.
- Attend Conferences and Webinars: Engage with the cyber security community by attending conferences, webinars, and workshops. Events like DEF CON, Black Hat, and RSA Conference offer insights into emerging threats and technologies.
- Network with Peers: Connect with other cyber security professionals through social media platforms like LinkedIn, forums, and local meetups. Engaging with peers can provide valuable insights and help you stay current with industry best practices.
Real-Life Experiences and Testimonials
Insights from Current Google Employees in Cyber Security Roles
- Employee Testimonials: Many current Google employees in cyber security roles highlight the company’s commitment to innovation and professional growth. For example, a Security Engineer might share how working on cutting-edge projects and collaborating with a team of experts has significantly advanced their skills and career. These employees often appreciate Google’s supportive work environment and access to state-of-the-art tools and resources.
- Work Culture and Environment: Employees frequently describe Google’s work culture as collaborative and dynamic. They emphasize the company’s focus on continuous learning and development, with opportunities to attend conferences, participate in training, and work on diverse and challenging projects. This environment fosters both personal and professional growth, making it an attractive place for cyber security professionals.
Personal Anecdotes and Tips for Prospective Applicants
- Navigating the Application Process: Current employees often suggest thoroughly researching the role and tailoring your application to highlight relevant skills and experiences. Personal anecdotes reveal that a well-crafted resume and a strong cover letter can make a significant difference in standing out to recruiters.
- Preparing for Interviews: Employees advise prospective applicants to prepare for technical interviews by practicing common problem-solving scenarios and staying updated on the latest cyber security trends. They also recommend showcasing not only technical expertise but also problem-solving abilities and a passion for security.
- Building a Network: Networking with current employees and participating in industry events can provide valuable insights and potentially improve your chances of securing an interview. Employees often note that connections and referrals can play a crucial role in the hiring process.
Conclusion
A career in cyber security at Google offers a unique blend of innovation, professional growth, and a supportive work environment. Google’s reputation as a leader in the industry, coupled with its commitment to cutting-edge security practices, makes it an ideal place for cyber security professionals. By understanding the essential skills, navigating the application process, and preparing thoroughly, you can position yourself as a strong candidate.
Pursuing a career in cyber security at Google not only provides an opportunity to work with some of the brightest minds in the field but also allows you to contribute to safeguarding the digital landscape. If you’re passionate about cyber security and eager to make a difference, consider taking the next step towards joining Google’s dynamic team. Your journey to becoming a part of this leading company in cyber security could start with the insights and tips shared here.



